Perhaps without realizing it, you are likely already very familiar with biometrics. The majority of modern cellphones and other mobile devices already have biometric sensors built-in, while airport security is increasingly adopting the technology as a way to identify people trying to gain entry to a country.
Once the preserve of James Bond-type spy movies, biometrics devices use physical characteristics to recognize a person – rather like we do in real life – but way, way more advanced. In our modern world, it is becoming increasingly important to secure data or block/allow access. While in days of old, simple passwords and keys did an admirable job, they are far too easy to lose or fall into the wrong hands – hence the rise in biometric security systems for everything from home/office security to mobile devices and even automobiles.
The problems with old-type security measures
Keys are great – but what if you lose them? Short of getting a locksmith to come let you in, you’ll have no choice but to break down the door (presuming you can). Also, keys can easily be copied should you lose, misplace them or have them stolen.
The same applies to traditional passwords – although one might convincingly argue passwords are even less secure since they can also be hacked.
As more and more of our lives move online, cyber and real-world crime has increased, giving rise to the need for more advanced forms of security for Access Control solutions. Digitally encrypted cards are an option – and a good one at that – but if you want true security, biometrics sit at the top of the tree.
In biometrics, you are the ‘key’
Rather than requiring a key of some sort (whether that be an actual, physical key or a password), biometrics make the person the key by studying and storing characteristics. If you’re not who you claim to be, you simply won’t get access.
Biometric security systems typically use two types of ‘key’ unique to the person:
-
Behavioral characteristics: Such as the tone and depth of your voice or the speed and pattern of your typing or handwriting.
-
Physical characteristics: Including fingerprints, facial features or veins.
There are seven main types of biometric security system in use today offering varying levels of security: facial recognition, fingerprints, voiceprints, handwriting, hand/finger geometry, iris scanning and vein geometry.
The three stages and components of biometric security systems
Pretty much all biometric security systems involve three stages to set up. While there might be minor differences from system to system, almost all biometrics require the following processes:
User registration with the system: Users register with the system, typically using an ID number or just their name to set up a base profile. Once registered, the specific character trait is attached to their profile (e.g. fingerprint or facial scan). This stage requires a scanner or sensor to capture the data.
Transfer and data storage: The basic profile of the user is stored in a database. However, unlike the way systems are commonly presented in spy films and the like, the original image isn’t normally stored. Rather systems translate the image into a computer-readable graph or code. It is also not uncommon for this data to be saved onto a card for back-up. This stage requires a computer and a hard drive.
Evaluation and contrast: When the user next attempts to gain access, the system will compare the graph or code data stored on file with the “image” of the user presented before it (again, translated to graph data). If the traits match, it will allow access. If not, the user will be locked out. This comparison process requires software to accurately gauge possible differences between the live profile and the stored profile.
Once a biometric system is set up, it can provide unrivaled protection, considerably more robust than other methods of security. By far the most common types of biometric security are:
Fingerprint scanners
Humans already have a highly personalized ID “card”. Our fingerprints are so unique that scientists believe there is almost zero chance that identical prints have existed in the history of human existence. Consequently, fingerprint scanners are a highly secure method of determining an individual’s credentials. There are many ways to scan fingerprints. However, by far the two most common methods are:
Optical scanners: Optical scanners work in a similar way to digital cameras and camcorders and use a Charged Coupled Device (CCD) to capture an image consisting of millions of pixels. In simple terms, this image is then stored and compared to a new image captured when the user next presents their finger for scanning, checking for enough similarities between the images to ascertain the prints belong to the same person.
Capacitance scanners: The technology behind capacitance scanners is highly complex and would justify an article in itself. However, in simple terms, these scanners use sensors to build a digital map of the ridges and valleys in a fingerprint (based on the subtle differences of capacitance between the two). Therefore, this method of scanning requires the user’s actual finger to gain entry (since no two fingerprints are identical). For this reason, capacitance scanners are normally regarded as being more secure than optical scanners.
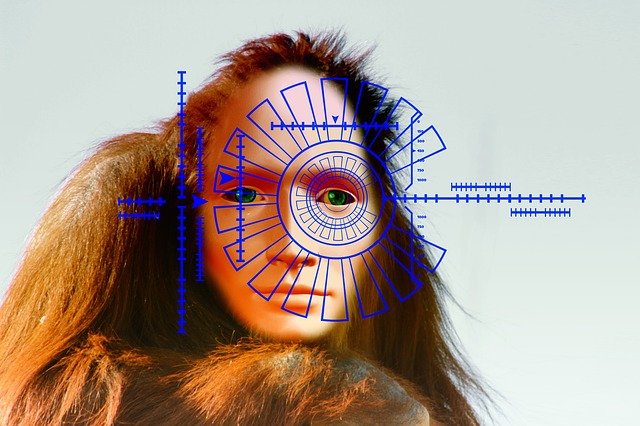
Facial recognition systems
Humans have always possessed the innate ability to recognize individuals by their features. However, it’s only very recently that scientists have managed to teach computers to do the same.
Work on computer facial recognition started in the 1960s, based on the premise that all human faces have distinguishable nodal points – features that differentiate us from each other. These include (but are not limited to) the width and length of the nose, the distance between the eyes, the length and shape of the jawline, the roundness and depth of the eye sockets and the softness of the cheekbones.
Using these key characteristics, it is possible to build up a facial profile that can be used for comparison purposes with a scanner. Facial recognition systems have recently started incorporating 3D profiling for greater accuracy, scanning the face from multiple angles at once to build a more complete and accurate image.
Iris scanners
Just like our fingerprints, human eyes are pretty much unique – so much so, it’s estimated the chances of mistaking one iris for another is around 1 in 10 to the power of 78.
Iris scanning works in a similar way to optical fingerprint scanning, using a CCD to capture an image of the eye. However, iris scanners also use near-infrared light to capture a high-contrast image of the patterns within the iris of the eye, resulting in around 200 unique reference points for comparison. For this reason, iris scanning is becoming increasingly common for high-security installations and applications.









![Watch Video Now on xiaohongshu.com [以色列Elevatione perfectio X美容仪 perfectio X 全新仪器黑科技了解下]](https://www.techburgeon.com/wp-content/uploads/2019/07/perfectiox-singapore-150x150.jpg)
